When Using Kerberos, What Is The Purpose Of A Ticket?
Co-ordinate to myth, Kerberos (you might know him as Cerberus) guards the Gates to the Underworld. He's a big three headed dog with a snake for a tail and a really bad atmosphere.
In the modern world, MIT Computer Scientists used the name and visual of Kerberos for their computer network authentication protocol. Kerberos uses symmetric key cryptography and requires trusted 3rd-party potency to verify user identities. Since Kerberos requires 3 entities to authenticate and has an first-class rails tape of making calculating safer, the name really does fit.
Get the Costless Pentesting Active
Directory Environments eastward-book
What is Kerberos?
Kerberos authentication is currently the default authorization technology used past Microsoft Windows, and implementations of Kerberos exist in Apple tree Os, FreeBSD, UNIX, and Linux.
Microsoft introduced their version of Kerberos in Windows2000. It has also become a standard for websites and Unmarried-Sign-On implementations across platforms. The Kerberos Consortium maintains Kerberos as an open up-source project.
Kerberos is a vast improvement on previous authorization technologies. The strong cryptography and third-party ticket authorization brand information technology much more hard for cybercriminals to infiltrate your network. Information technology is not totally without flaws, and in club to defend confronting those flaws, you need to first sympathize them.
Kerberos has made the internet and its denizens more secure, and enables users to practise more work on the Internet and in the office without compromising safety.
What is the difference between Kerberos and NTLM?
Before Kerberos, Microsoft used an authentication engineering chosen NTLM. NTLM stands for NT Lan Director and is a challenge-response authentication protocol. The target computer or domain controller challenge and check the countersign, and store password hashes for continued use.
The biggest divergence betwixt the two systems is the 3rd-party verification and stronger encryption adequacy in Kerberos. This actress footstep in the process provides a pregnant additional layer of security over NTLM.
NTLM systems can go hacked in a affair of hours these days: information technology's only older technology, and you shouldn't rely upon NTLM to protect sensitive data.
How practice you authenticate with Kerberos?
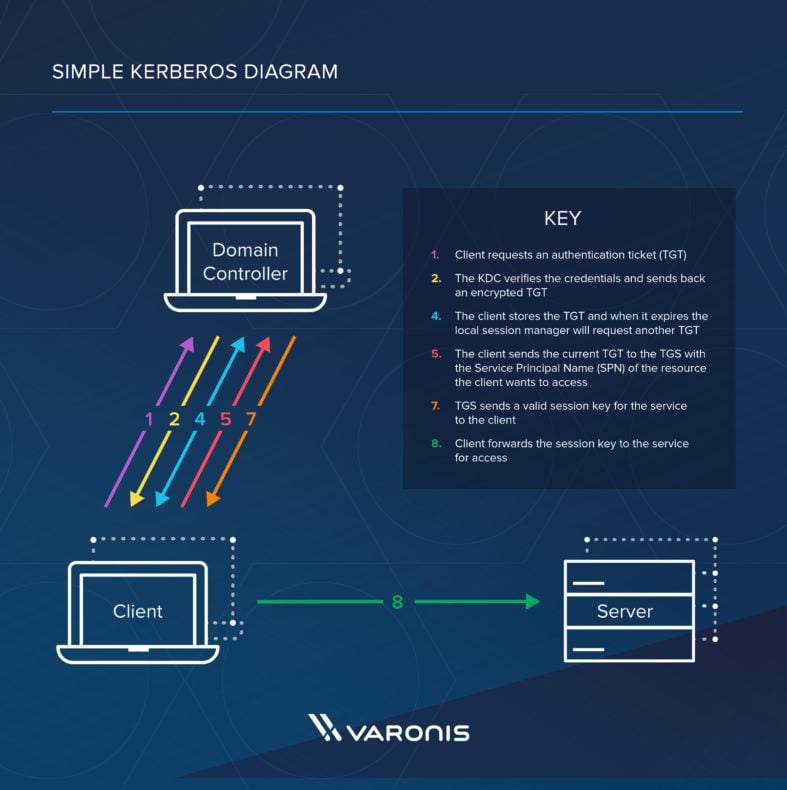
Here are the about basic steps taken to authenticate in a Kerberized surroundings.
- Client requests an authentication ticket (TGT) from the Key Distribution Center (KDC)
- The KDC verifies the credentials and sends dorsum an encrypted TGT and session key
- The TGT is encrypted using the Ticket Granting Service (TGS) secret primal
- The client stores the TGT and when it expires the local session manager volition asking another TGT (this process is transparent to the user)
If the Client is requesting access to a service or other resource on the network, this is the process:
- The client sends the electric current TGT to the TGS with the Service Principal Proper name (SPN) of the resource the customer wants to access
- The KDC verifies the TGT of the user and that the user has access to the service
- TGS sends a valid session key for the service to the customer
- Client forrad the session key to the service to prove the user has access, and the service grants access.
Can Kerberos Be Hacked?
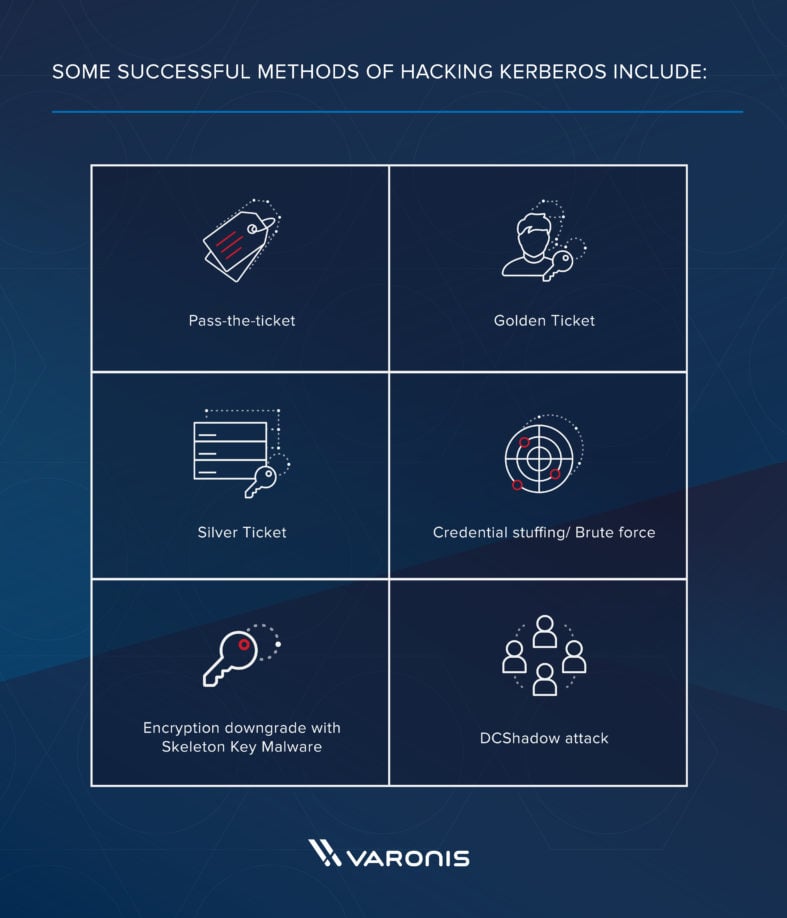
Aye. Considering it is one of the virtually widely used authentication protocols, hackers have developed several means to cleft into Kerberos. Nigh of these hacks accept reward of a vulnerability, weak passwords, or malware – sometimes a combination of all three. Some of the more than successful methods of hacking Kerberos include:
- Pass-the-ticket: the procedure of forging a session key and presenting that forgery to the resource as credentials
- Gilt Ticket: A ticket that grants a user domain admin access
- Silverish Ticket: A forged ticket that grants access to a service
- Credential stuffing/ Brute forcefulness: automated continued attempts to estimate a password
- Encryption downgrade with Skeleton Key Malware: A malware that can bypass Kerberos, only the attack must take Admin access
- DCShadow attack: a new attack where attackers gain enough admission within a network to set up their ain DC to use in further infiltration
Is Kerberos Obsolete?
Kerberos is far from obsolete and has proven itself an adequate security-access control protocol, despite attackers' ability to crevice it. The primary advantage of Kerberos is the ability to employ strong encryption algorithms to protect passwords and hallmark tickets. With today'south computers, whatever brute force attack of the AES encryption protocol used by the current version of Kerberos will take approximately longer than this solar system has left to survive. Suffice to say: Kerberos is going to exist around for a while in ane form or another.
What is going to replace Kerberos?
There are no real contenders to replace Kerberos in the pipeline. Well-nigh of the advancements in security are to protect your password or provide a different method of validating who you are to Kerberos. Kerberos is nonetheless the back-end applied science. Kerberos excels at Single-Sign-On (SSO), which makes information technology much more than usable in a modern cyberspace based and connected workplace. With SSO y'all prove your identity once to Kerberos, so Kerberos passes your TGT to other services or machines as proof of your identity.
The weakest link in the Kerberos concatenation is the password. Passwords tin can exist fauna-force cracked or stolen by phishing attacks. For this reason, Multi-Cistron Hallmark (MFA) is condign more popular to protect online identities. With MFA, you need the password and something else – a randomized token, mobile phone, email, thumbprint, retina browse, facial recognition, etc. – to testify that you are in fact who yous are telling Kerberos you are.
How does Varonis monitor Kerberos?
Varonis monitors Active Directory domains for Kerberos attacks, privilege escalations, fauna forcefulness attacks, and more. Our security analytics combines user events, security events, and perimeter telemetry – to notice and alert on potential attacks and security vulnerabilities.
Sample Varonis threat models that aid notice Kerberos attacks include:
- Potential pass-the-ticket assault: access to a resource was requested without proper hallmark, bypassing the Kerberos protocol.
- Failed privilege escalation detected via vulnerability in Kerberos: an attacker tried to drag their privileges via Kerberos vulnerability.
- Potential brute-strength attack targeting a specific account: an unusual corporeality of authentication failures from a single IP address by a single user has occurred.
- Security certificate activity by not-administrators: Activity was detected on certification files by a user who is not an ambassador – potentially indicating an attacker trying to steal signatures.
- …and that'due south just the beginning!
Discover how Varonis detects Kerberos attacks for real with a 1:1 demo today – and arrive touch to learn out more about our threat models.

Jeff Petters
Jeff has been working on computers since his Dad brought home an IBM PC 8086 with dual disk drives. Researching and writing about data security is his dream task.
When Using Kerberos, What Is The Purpose Of A Ticket?,
Source: https://www.varonis.com/blog/kerberos-authentication-explained
Posted by: samonsatrom1955.blogspot.com


0 Response to "When Using Kerberos, What Is The Purpose Of A Ticket?"
Post a Comment